Over the next 12 days, this mini-series will share short, real-world security lessons from recent incidents, and industry trends. Each post will focus on a single topic, highlight what happened, and outline practical steps organisations can take to reduce risk. The aim is to provide short, accessible insights that reflect how security challenges are unfolding … Continue reading 40M Voters Exposed: Security Lessons from a Major Breach
Author: Taylor Carr McAuley
JLR Cyberattack: Lessons from a Major Manufacturing Crisis
Jaguar Land Rover (JLR), one of the UK's most iconic car manufacturers, suffered a crippling cyber attack in late August 2025. This incident halted production, crippled its supply chain, and cost tens of millions of pounds per week. The attack highlights the vulnerability of modern manufacturing networks, especially as they become more digital and interconnected. … Continue reading JLR Cyberattack: Lessons from a Major Manufacturing Crisis
AI-Enhanced Phishing: New Challenges for Cybersecurity
With the rise of AI, phishing scams have evolved from obvious traps to highly sophisticated communications that blend seamlessly into inboxes. Attackers utilise large language models, voice cloning, and deepfakes, making phishing more difficult to detect. To combat these threats, companies must enhance technical controls, provide awareness training, and establish verification protocols.
Breaking the Firewall: A Young Woman’s Guide to Thriving in STEM
When I first stepped into cyber security, I noticed something straight away. I was often the only woman in the room. I was usually the youngest too. It wasn't a bad thing, but it did make me hyper-aware of how few of us there were. Entering STEM (science, technology, engineering, and maths) isn't about fitting … Continue reading Breaking the Firewall: A Young Woman’s Guide to Thriving in STEM
The Hidden Cost of Convenience: How Shadow IT Threatens Enterprise Security
In an era defined by remote work, rapid digital transformation, and rising user expectations, employees increasingly turn to their own tools to stay productive. Whether it's using personal file-sharing apps, communication platforms, or even AI assistants, this informal adoption of unsanctioned technology - known as Shadow IT - introduces serious risks to enterprise security. Shadow … Continue reading The Hidden Cost of Convenience: How Shadow IT Threatens Enterprise Security
Cyber Security Careers: Find Your Ideal Role Today
So, you're thinking about cyber security? Maybe you're curious about career-switching, just starting out, or trying to figure out why everyone keeps saying 'blue team' like it's a Marvel squad. Either way, welcome to the chaotic good side of tech. The truth? Cyber security is not just one job. It's a whole universe of roles, … Continue reading Cyber Security Careers: Find Your Ideal Role Today
Essential Tips to Secure Your Social Media Accounts
Let's be real, our social media accounts are basically an extension of our lives. Whether it's Instagram, TikTok, X, or Facebook, these platforms hold everything from pictures to business DMs. So imagine waking up one day to find you've been hacked. Nightmare, right?! Unfortunately, it's more common than you'd think. Hackers are getting smarter, and … Continue reading Essential Tips to Secure Your Social Media Accounts
Cyber Security Trends for 2025: AI, Crime, and Compliance
Cyber Security in 2025 feels like standing at a crossroads. The pace of change is relentless - and Cyber Security is now no longer 'just an IT problem'. It's now a leadership, legal, and cultural issue. In my almost 8 years within the industry, I have witnessed the landscape change at an extremely fast pace. … Continue reading Cyber Security Trends for 2025: AI, Crime, and Compliance
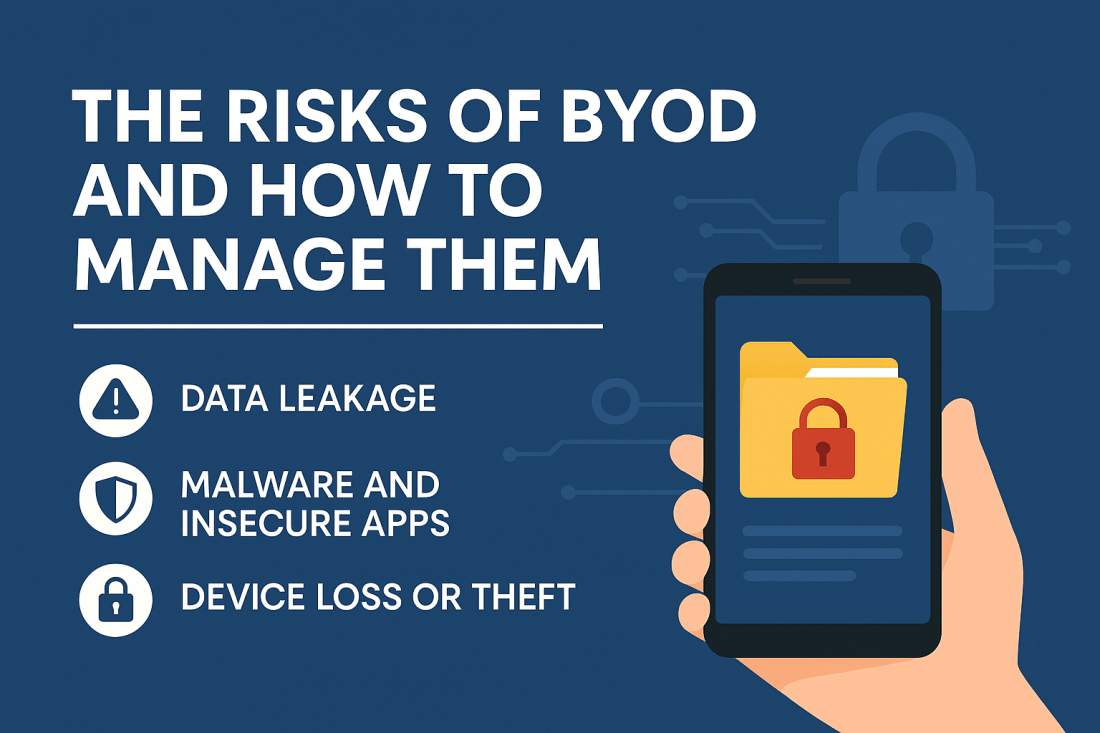
The Dangers of BYOD: Risks Every Company Must Address
Bring Your Own Device (BYOD) has become increasingly common in today's digital workplace. This trend is particularly noticeable with the rise of remote and hybrid working. BYOD refers to the policy of allowing employees to use their personal devices - such as smartphones, tablets, and laptops - for work purposes (NIST, 2020). However, in my … Continue reading The Dangers of BYOD: Risks Every Company Must Address
Why Cyber Security Teams Need MITRE ATT&CK Framework
In a digital world where cyber attacks are becoming more targeted and sophisticated, organisations need a proactive, intelligence-led approach to defending their systems. One such resource is the MITRE ATT&CK Framework - a globally recongised and extensively adopted knowledge base of adversary tactics and techniques, which has become a foundational element of modern cyber security … Continue reading Why Cyber Security Teams Need MITRE ATT&CK Framework