Most security teams are busy. That's a given. There is always another project, audit or incident competing for attention. In that environment, it is dangerously easy to confuse activity with impact. Everyone is working hard, but it is not always clear whether the organisation is genuinely safer or simply more exhausted. A high‑impact security team … Continue reading From Firefighting to Forward‑Looking: Building a High‑Impact Security Team
Tag: Vulnerability
When Shared Responsibility Means No Responsibility
Modern security environments are built on shared responsibility. Cloud providers, third-parties, internal teams, and business leaders all play a role in managing risk. In theory, this model enables scale and flexibility. In practice, it often creates gaps. Many security failures are not caused by a lack of controls or awareness, but by uncertainty over who … Continue reading When Shared Responsibility Means No Responsibility
Understanding Modern Threat Actors: Perspectives & Strategies
Threat actors are not a single, uniform group. They range from financially motivated gangs to state-linked operators and loosely structured criminal ecosystems, each with different objectives and levels of sophistication. Understanding a few prominent examples can assist teams in thinking more clearly about how attackers operate. This helps identify where defences are likely to be … Continue reading Understanding Modern Threat Actors: Perspectives & Strategies
Transforming Security: From Blocker to Business Enabler
Security teams are often seen as the function that slows work down, adds extra steps, or blocks ideas at the last minute. That perception does not just impact team relationships; it directly affect how early people involve security and how willing they are to act on advice. Shifting security from "blocker" to "business enabler" is … Continue reading Transforming Security: From Blocker to Business Enabler
Enhancing Incident Response Through Effective Communication
When a security incident occurs, technical response often becomes the immediate focus - isolating systems, analysing logs, restoring services. However, the effectiveness of an incident response also depends on how well teams communicate under time pressure and uncertainty. Clear, structured communication helps people understand priorities, coordinate activity, and avoidable delays. Communication will not remove risk … Continue reading Enhancing Incident Response Through Effective Communication
40M Voters Exposed: Security Lessons from a Major Breach
Over the next 12 days, this mini-series will share short, real-world security lessons from recent incidents, and industry trends. Each post will focus on a single topic, highlight what happened, and outline practical steps organisations can take to reduce risk. The aim is to provide short, accessible insights that reflect how security challenges are unfolding … Continue reading 40M Voters Exposed: Security Lessons from a Major Breach
The Hidden Cost of Convenience: How Shadow IT Threatens Enterprise Security
In an era defined by remote work, rapid digital transformation, and rising user expectations, employees increasingly turn to their own tools to stay productive. Whether it's using personal file-sharing apps, communication platforms, or even AI assistants, this informal adoption of unsanctioned technology - known as Shadow IT - introduces serious risks to enterprise security. Shadow … Continue reading The Hidden Cost of Convenience: How Shadow IT Threatens Enterprise Security
Cyber Security Careers: Find Your Ideal Role Today
So, you're thinking about cyber security? Maybe you're curious about career-switching, just starting out, or trying to figure out why everyone keeps saying 'blue team' like it's a Marvel squad. Either way, welcome to the chaotic good side of tech. The truth? Cyber security is not just one job. It's a whole universe of roles, … Continue reading Cyber Security Careers: Find Your Ideal Role Today
Cyber Security Trends for 2025: AI, Crime, and Compliance
Cyber Security in 2025 feels like standing at a crossroads. The pace of change is relentless - and Cyber Security is now no longer 'just an IT problem'. It's now a leadership, legal, and cultural issue. In my almost 8 years within the industry, I have witnessed the landscape change at an extremely fast pace. … Continue reading Cyber Security Trends for 2025: AI, Crime, and Compliance
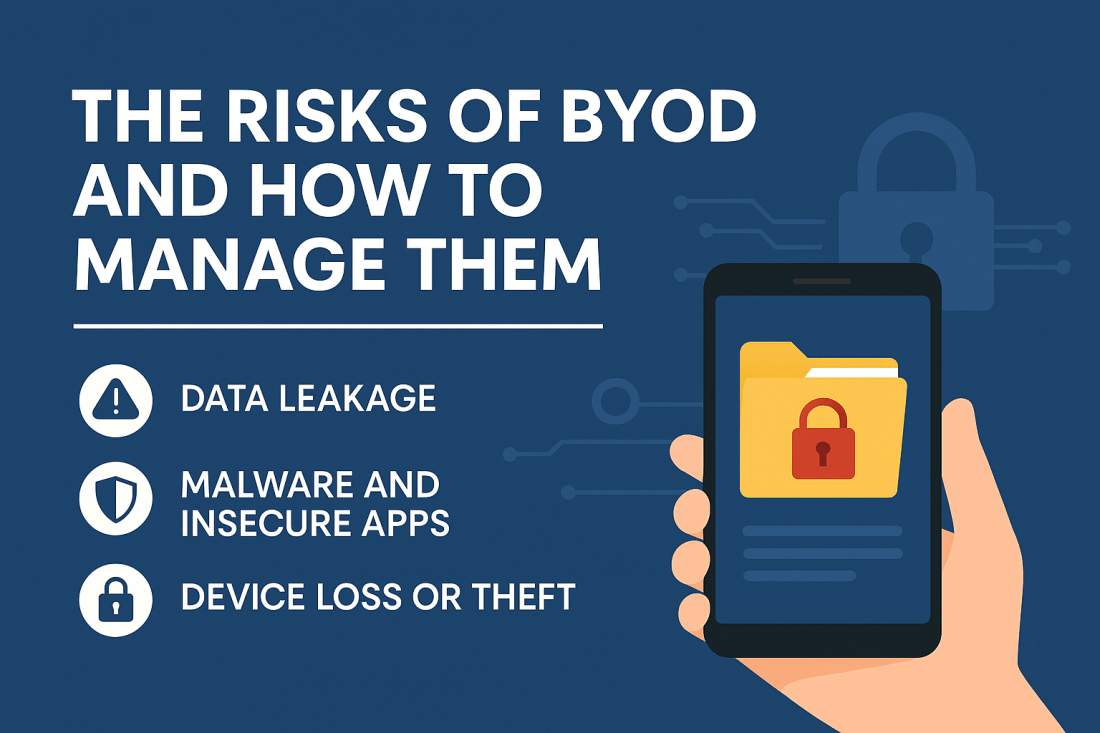
The Dangers of BYOD: Risks Every Company Must Address
Bring Your Own Device (BYOD) has become increasingly common in today's digital workplace. This trend is particularly noticeable with the rise of remote and hybrid working. BYOD refers to the policy of allowing employees to use their personal devices - such as smartphones, tablets, and laptops - for work purposes (NIST, 2020). However, in my … Continue reading The Dangers of BYOD: Risks Every Company Must Address